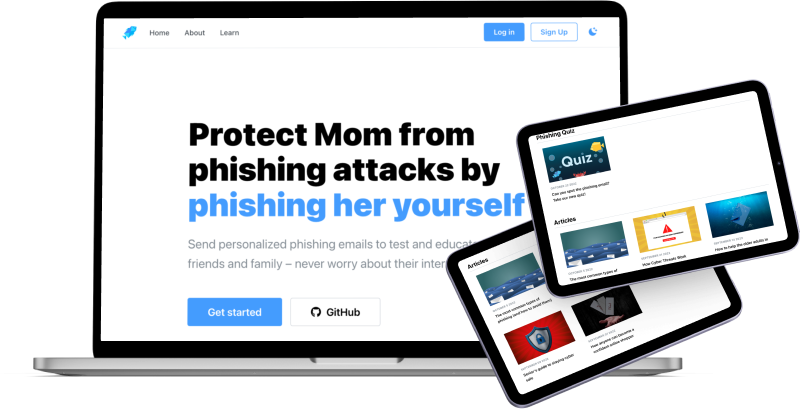
We removed the signup form on the landing page; instead, the signup/login buttons were only located on the navigation bar so that it felt less prominent.
We also simplified the services Phished provided and added card components to showcase so that the users could see what they would sign up for at a glance.

Through user testing, we’ve learned that some users struggled to create phishing-looking emails without a template. Thus, we created additional 5 email templates, including a google doc invitation, Facebook notification, LinkedIn confirmation, new device access notification, and payment notification.
When the targets click on the link in the email, we track the event and display the results in a dashboard to monitor the number of targets who fell for their campaign. In case a target falls for the phishing email, we redirect them to our learn page to educate them about the phishing email and how to avoid it in the future.
On the learn page, we provided quizzes and articles related to phishing emails. The quiz delivered several examples of emails containing common patterns and characteristics of phishing emails that users could receive in real life. Articles were additional resources to promote better security practices and learn how to improve users’ awareness of cyber threats.
In the mid-fi prototype, we hardcoded graphs and statistics on the test user account. However, at the end of the development, we couldn't verify if the data was accurate due to insufficient test accounts.
The current version shows the preview of a phishing email campaign in plain text despite different styles of templates. This preview might make it less intuitive for users to envision how the email would look when the phishee received it.
It also provides a plain text email as a style of phishing email for both campaigns and the quiz. If we had more time to work, we would categorize different types of emails such as financial institutes, social media, security alerts, and purchase confirmation to give more flexibility and liberty to design the campaigns and tailor their learning contents.